Fidelis
Fidelis Elevate provides a streamlined security stack integrates network visibility,
data loss prevention, deception, and endpoint detection and response into one unified solution.
Fidelis Elevate
Detect & Respond to Threats
Fidelis Network goes well beyond its name by uniting real-time content analysis from five sensor locations (gateways, internal networks, email, web, and cloud) with DLP for network, email, and web traffic, plus email security including OCR of text within images. Context rich metadata also enables detection and threat hunting across a cyber terrain mapped continuously by Fidelis Network with asset profiling and classification. Open by design for threat intelligence feeds, it is the modern day core of your security stack.
Advanced Malware Protection (APT)
Real-time Detection and Prevention

– Network Traffic Inspection: All 0~65535 port & protocols
– Detect and prevent unknown protocols and abnormal URL request
– DNS Anomaly Monitor, detect potential malicious DNS activity
– Packet content identification and analyze malicious program by uncompressing unlimited times
– MDE for Real-time threat
– Support YARA rule with integration of network threat feed
– Rapid detection for known and unknown malicious program by Emulation
Fidelis Network was named by Gartner as a Visionary in DLP and was recently noted among the top Network Traffic Analysis vendors.
Data Loss Protection (DLP)
Real-time Detection and DLP

-Real-time detection to prevent data loss
– Support all protocols and ports (0~65535) detection
– Customized prevention policies for specified IP ranges and masks


Fidelis Endpoint
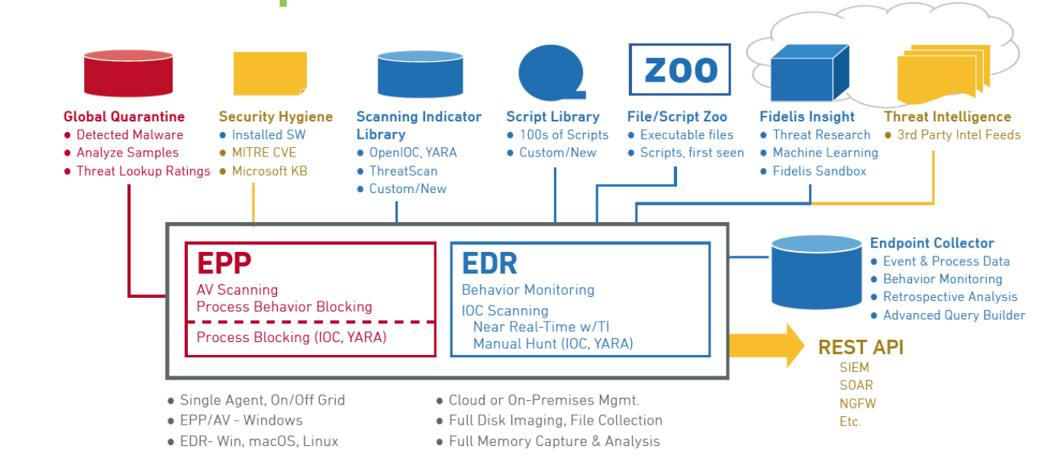
Fidelis Endpoint provides prevention (red), detection and response (blue), and third-party intelligence and integration (tan) in a single agent with on/off grid defenses.
Best-of-Breed
Across 7 Critical Areas in a Single Solution (and 1 Agent)
– EDR, EPP, System Management, Forensics – all via a single management and investigation UI
– Visibility of what’s on your endpoints and all endpoint activity
– Real-time threat detection and proactive hunting
– Timeline view of malware and endpoint behaviors
– Real-time and historical validation and investigation
– Remote forensics: memory analysis, collection, full disk imaging
– Out-of-the-box and customizable remediation
– Seamless integration, automation and correlation
– Easy integration with Fidelis Network and SIEMs
– Managed in the Cloud & On-Prem

interest in our product or service ?
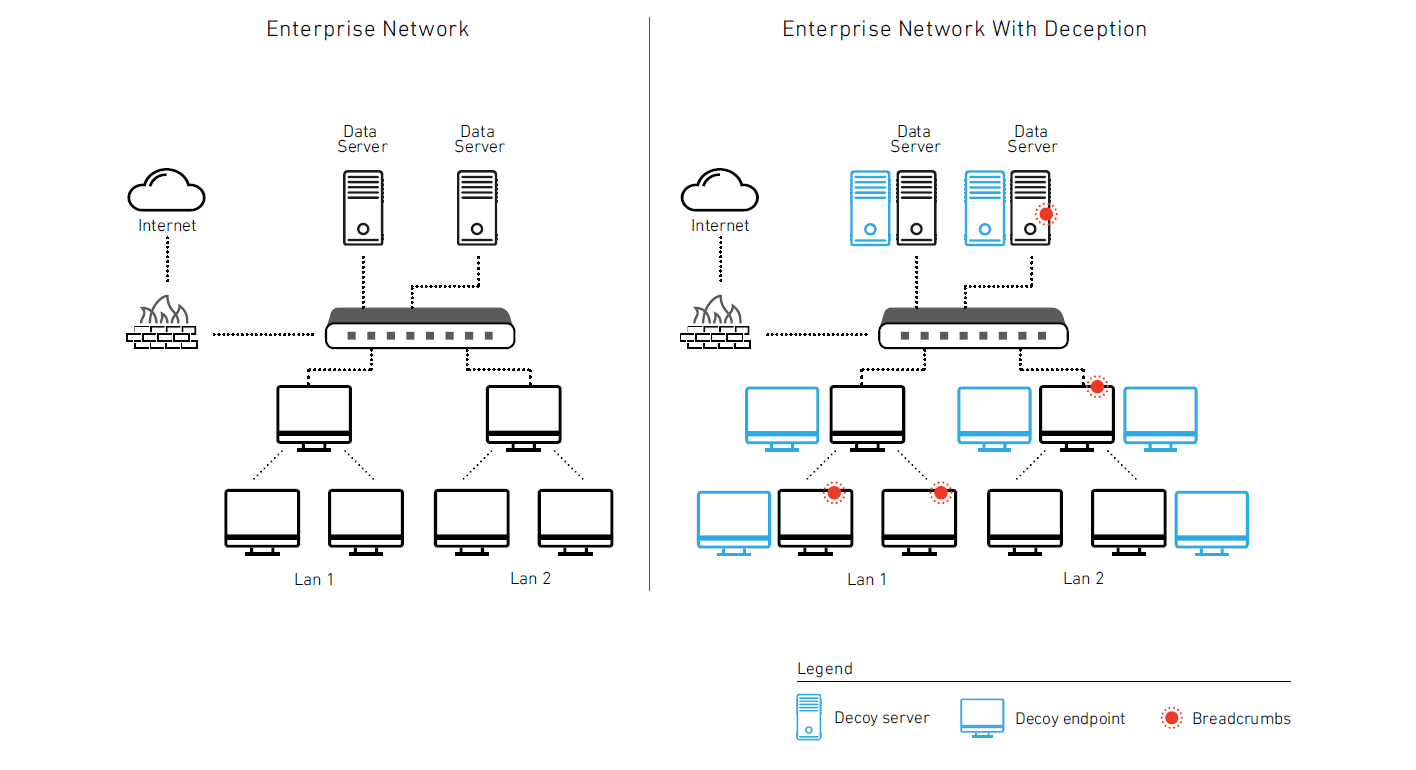
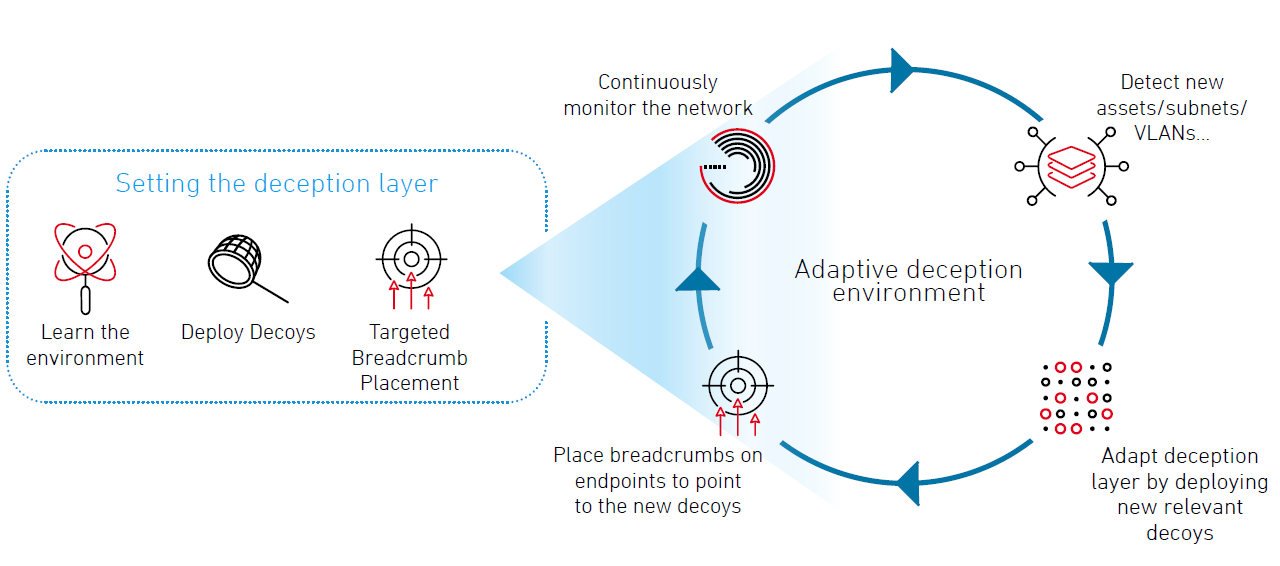
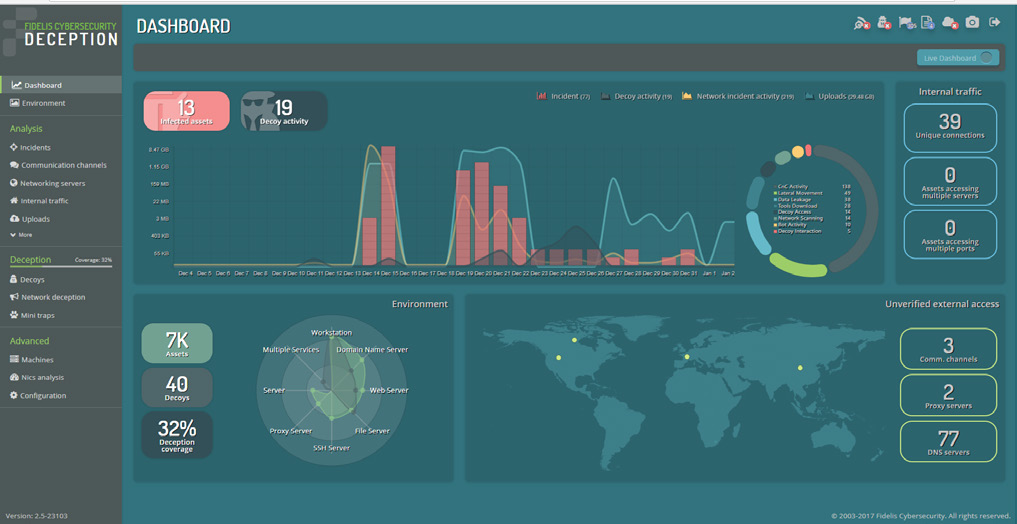
Fidelis Deception
Best-of-Breed
Deception with a Wide Array of Decoys and Breadcrumbs
– EDR, EPP, System Management, Forensics – all via a single management and investigation UI
– Visibility of what’s on your endpoints and all endpoint activity
– Real-time threat detection and proactive hunting
– Timeline view of malware and endpoint behaviors
– Real-time and historical validation and investigation
– Remote forensics: memory analysis, collection, full disk imaging
– Out-of-the-box and customizable remediation
– Seamless integration, automation and correlation
– Easy integration with Fidelis Network and SIEMs
– Managed in the Cloud & On-Prem
Fidelis Matadata
Record and analyze traffic at same time and store at Metadata database
Finding incident by simply search with keyword
– 12 types of application
– Customized searching criteria
– Provide analyzed information based on category to reduce missing or misjudment
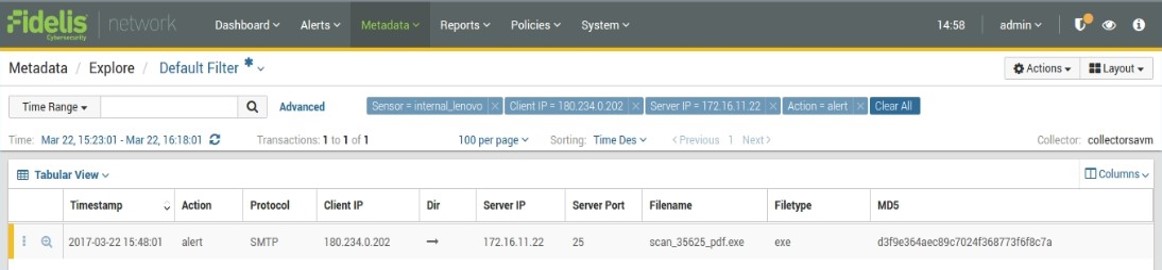
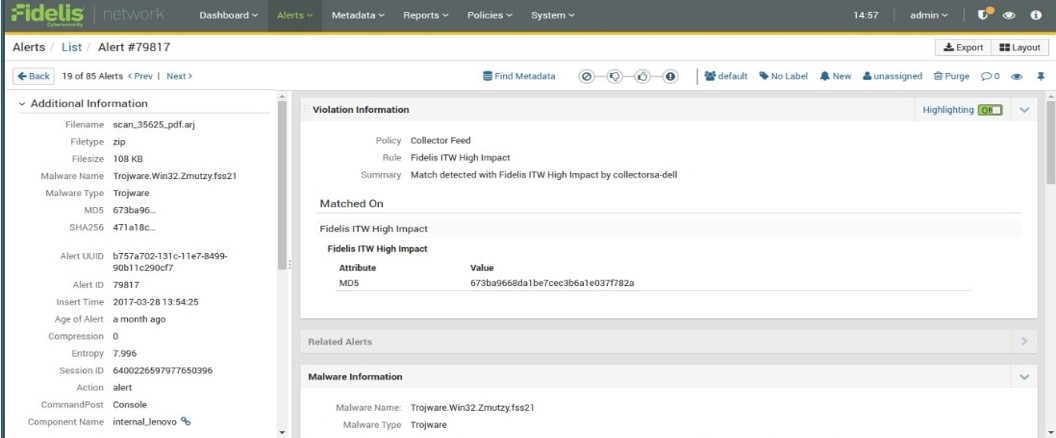
Matadata Example
- At 22-Mar, Fidelis didn’t detect malicious attack without signatures at threat intelligent
- But Fidelis recorded the sequent attack at Metadata database
- When threat intelligent is updated in 28-Mar, system is able to find the attack and alert by historical analysis